Blog: News, Tips, Stories & More
Enhancing Hotel Infrastructure: The Key to Superior Guest Experiences
Hotel operators face the challenge of not only meeting but exceeding guest expectations. One way to achieve this is by ensuring that the hotel’s infrastructure is up-to-date and capable of providing a seamless and secure...
Password safety tips for your employees during this holiday season
Password safety tips for your employees The holiday season is in full swing, and for many businesses, it’s the busiest time of the year. Amidst the chaos of long lines and increased foot traffic in...
Managing your technology shouldn’t be the last thing on your company’s holiday shopping list
We manage your technology so you can focus on your business It’s the holiday season, and many businesses, like yours, are busy with shoppers and the rush of activity to serve those customers. However, one...
Avoid Sponsored Search Results
Many times, the sponsored results are not what they appear. They are often malicious or phishing sites designed to trick the user. We’ve seen an uptick of this behavior recently. Users search for ‘amazon’ on...
Cyber Liability Insurance: A Shield Against the Digital Dark Arts
Businesses of all sizes are under constant threat from cyber attacks. Ransomware, data breaches, and other malicious activity can have a devastating impact on a business, leading to financial losses, reputational damage, and even legal...
Cannabis & IT – Proper Protection is Essential
As the legal pharmaceutical and recreational cannabis industries continue to grow and evolve, businesses in these sectors are facing increasing pressure to stay ahead of the curve and remain competitive. One crucial aspect of this...
Leveraging Solid-state drives (SSDs) vs physical hard disk drives (HDDs)
Solid-state drives (SSDs) and physical hard disk drives (HDDs) are two types of computer storage that have distinct differences. In recent years, SSDs have gained popularity due to their faster performance and reliability compared to...
Benefits of a Professional Email Service (Like Google Workspace or Microsoft 365)
Email is an essential tool for businesses to communicate with their customers, vendors, and employees. However, choosing the right email service can be a daunting task, especially for small businesses that are just starting. When...
Everyone is Talking About ChatGPT: The Rise of OpenAI’s Language Model
Have you heard about ChatGPT? It’s the language model developed by OpenAI that’s taking the tech world by storm. In this blog post, we’ll explore why ChatGPT is generating so much buzz and why it’s...
The Concerns Surrounding AI in Technology
Artificial Intelligence (AI) has the potential to revolutionize the way we live and work, but it also raises important ethical and societal concerns. As AI technology becomes increasingly advanced and widespread, it is crucial to...
Password Complexity and Two-Factor Authentication: Essential Tools for Online Security
In today’s digital age, it is more important than ever to ensure the security of our online accounts. One of the most basic and essential steps we can take towards achieving this is by using...
The Importance of Cloud Backups
As we all have online presence, both personal and professionally, data is a valuable commodity and the importance of having a secure backup solution cannot be overstated. With the increasing threat of hackers, natural disasters...
TikTok: What are the Dangers?
TikTok has become one of the most popular social media platforms in recent years, especially among younger users. However, its rapid rise to popularity has also raised concerns about privacy, security, and the influence it...
The Startling Statistics of Hacked Businesses and How to Protect Yours
Cyber attacks have become a major concern for businesses of all sizes. Every day, organizations are falling victim to hackers who use sophisticated tactics, such as ransomware, to steal sensitive data and hold it for...
Unifi Networking Hardware for Business: A Comprehensive Solution for Optimal Wifi, Security, Remote Management, and Performance
Reliable and fast internet connectivity is essential for success. Whether you’re managing a large corporation or a small startup, you need to ensure that your employees, customers, and partners have access to fast, secure, and...
Securing Your Conversations Online: The Importance of End-to-End Encryption, SSL, and Signal Chat
In today’s digital world, online conversations have become a primary mode of communication. From instant messaging and email to video conferencing and social media, we all use these platforms to communicate with others on a...
The Difference between EDR and Traditional Antivirus
In today’s world of rapidly evolving technology, the threat of cyberattacks is always present. This is why having robust security measures in place is essential to protect your devices and data. Two popular options for...
The Benefits of Managed IT Services for Businesses
In today’s technology-driven world, having a reliable and efficient IT infrastructure is crucial for businesses of all sizes. Managed IT services provide businesses with a cost-effective and efficient way to manage their IT needs, allowing...
4 Reasons To Use Content Filtering to Restrict Access to Non-Work-Related Sites
The internet is a portal to anywhere. Employees can use the browsers on their work computer for good reasons, such as doing research for a work project or looking up customer or lead information. They...
5 ways your business can benefit from managed IT services
Of all the reasons you started your business, running an IT environment probably wasn’tone of them. But the more you rely on digital tools to connect with customers, planschedules, keep records, process sales or whatever...
What is Advanced Web Protection?
Going Beyond Traditional Firewall & Content Filtering to Provide Comprehensive Web Traffic Security One wrong click of a mouse by one of your employees can give cybercriminals access to your critical workflow and data. With...
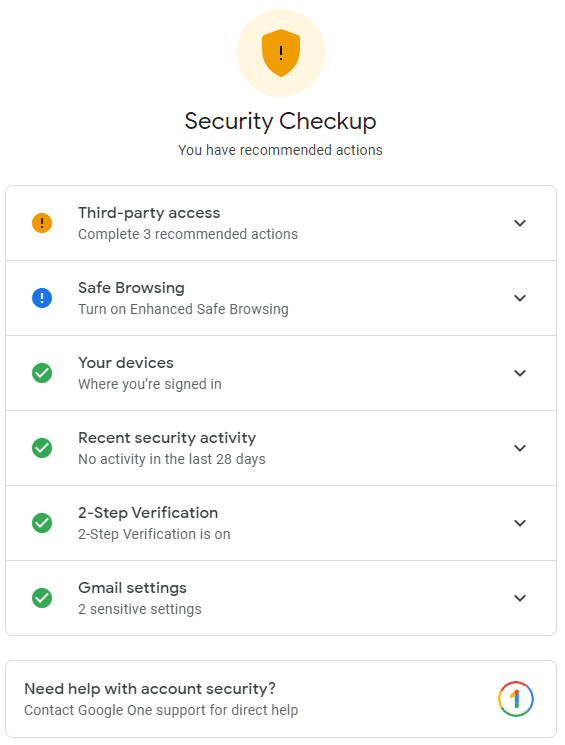
Help strengthen the security of your Google Account
Every so often, it’s a good idea to review your security. Whether is your network, your email or your credit cards, you should do a regular security check. Google offers users the ability to review...
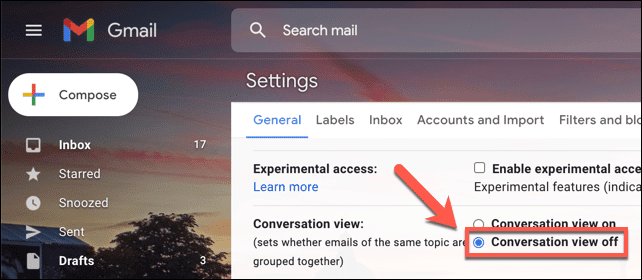
How to Disable Conversation View in Gmail
To disable “conversation view” (or grouped email threads) in Gmail on your Windows PC or Mac, you’ll need to do so from the Gmail website. Once you’ve signed in, click the settings gear icon in...
Learn How to Spot a Phishing Attempt
Phishing scams are one of the most popular ways that cybercriminals use to acquire highly sensitive information. Hackers will disguise themselves behind an email that seems like it is from a trusted sender. This way...
Security Threats for Businesses 5 of 5
Reusing Passwords Compromise Safety One of the main verification procedures that a business uses is passwords. But the biggest downfall is that more often than not people choose weak passwords that are easy to figure...
Security Threats for Businesses 4 of 5
An Infection From a Company User It only takes one angry employee to do some damage to the entire workplace with just a few clicks. They can install harmful malware or delete important files. The...
Security Threats for Businesses 3 of 5
Employees Have Little To No Cybersecurity Training Because technology is ever changing we all need to continue to learn and to stay up to date on the latest and innovative creations. Along with that hackers...
Security Threats for Businesses 2 of 5
Giving Admin Privileges to Employees on Their Computers Smaller Businesses will sometimes give their employees access to administrative privileges on their computers because they don’t have an IT team in place to manage their network...
Security Threats for Businesses 1 of 5
Installation of Malicious Software Hackers are very smart and they know exactly how to trick someone into clicking on a link and this is very dangerous because as soon as that link is activated malware...
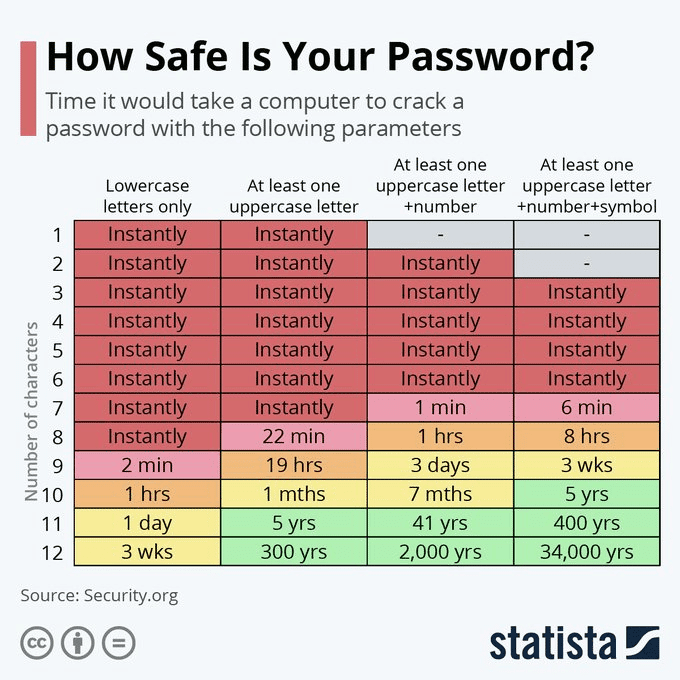
Is Your Password Secure Enough?
Nearly every website we visit today requires a username and password to be created. It becomes so hard to remember each one that we make. Even after being warned time and time again people still...
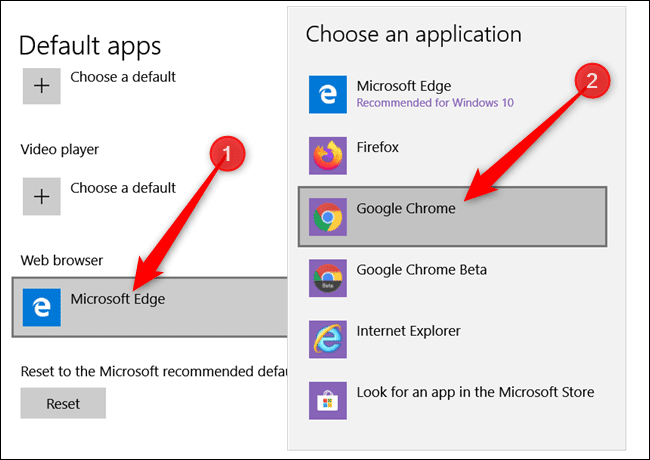
Change your default browser in Windows 10
Windows 10 comes with Microsoft Edge or Internet Explorer as the default internet browser. Many people prefer another browser, like Chrome or Firefox or even Safari. Whatever your choice, and whatever your current setting is...
Cybersecurity For Medical Information Is A Must
Medical service providers are one of the top companies that cybercriminals prey on. Hackers can acquire all sorts of information that they can then use illegally. This is why it is very important for healthcare...
7 Tips For Home Based Business Cybersecurity
Remote working, telecommuting, working from home are words that are becoming very popular when you ask someone about their job these days. While it does give more flexibility and freedom for employees who might be...
No post found